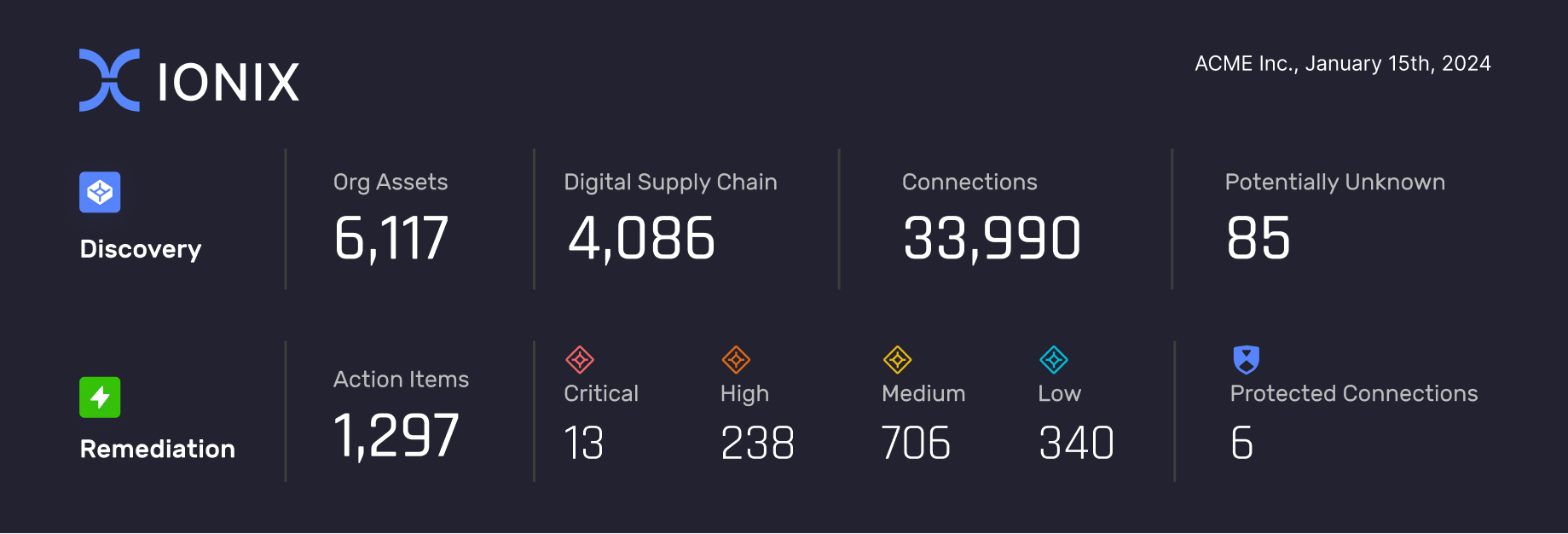
Internal Org Assets
Assets hosted in the organizational network (in their on-premise data centers or controlled cloud environments)
Get a comprehensive report of your complete attack surface exposure. The content below is excerpted from an actual attack surface exposure report from an IONIX customer.
Assets hosted in the organizational network (in their on-premise data centers or controlled cloud environments)
Assets hosted outside of the organizational network (hosting providers, non-controlled cloud environments and others)
Assets that the organization relies on, but does not own (Mail or DNS servers, Script Inclusion, APIs or others)
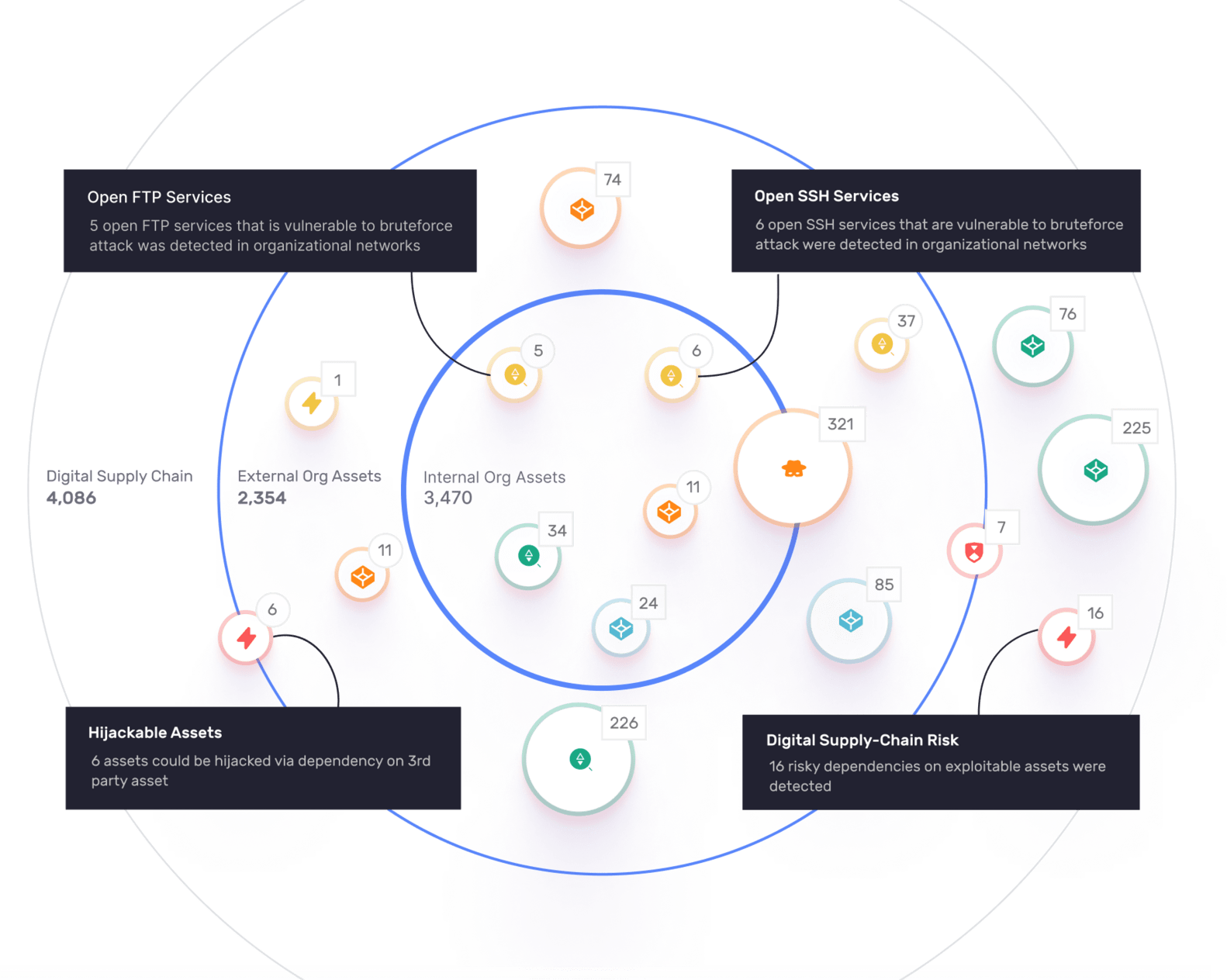
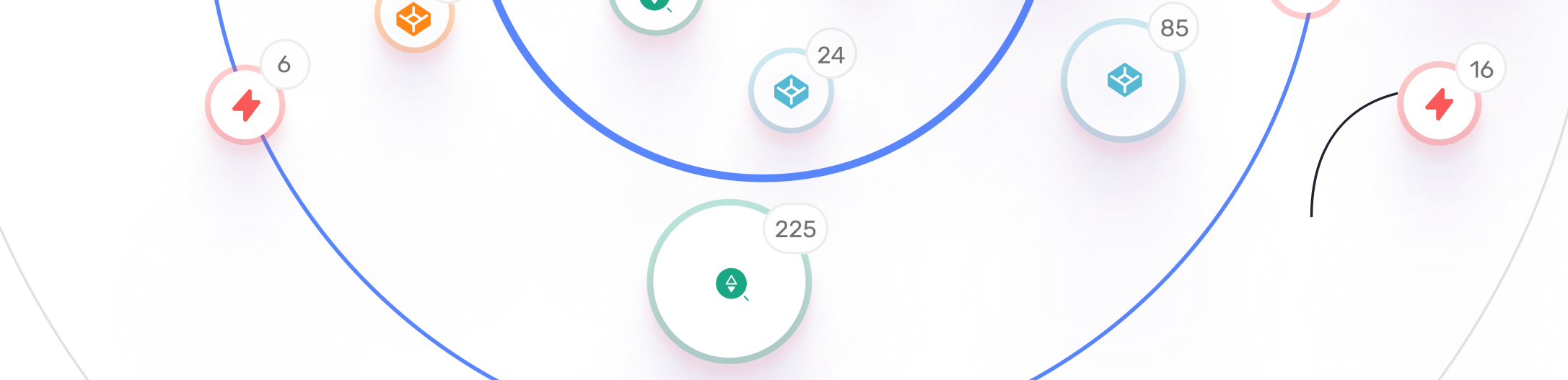
16 risky dependencies on exploitable assets were detected
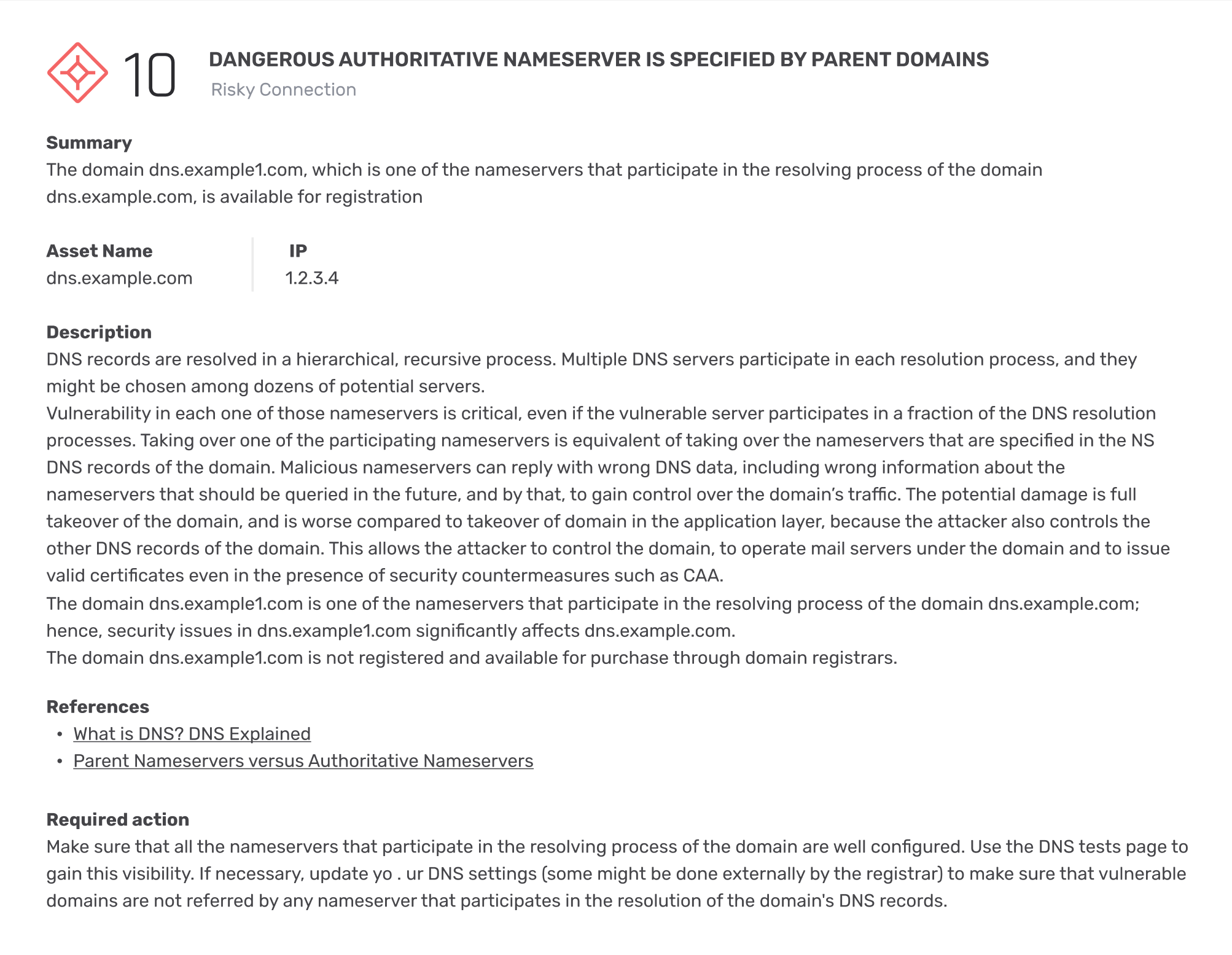
6 assets could be hijacked via a dependency on 3rd party asset
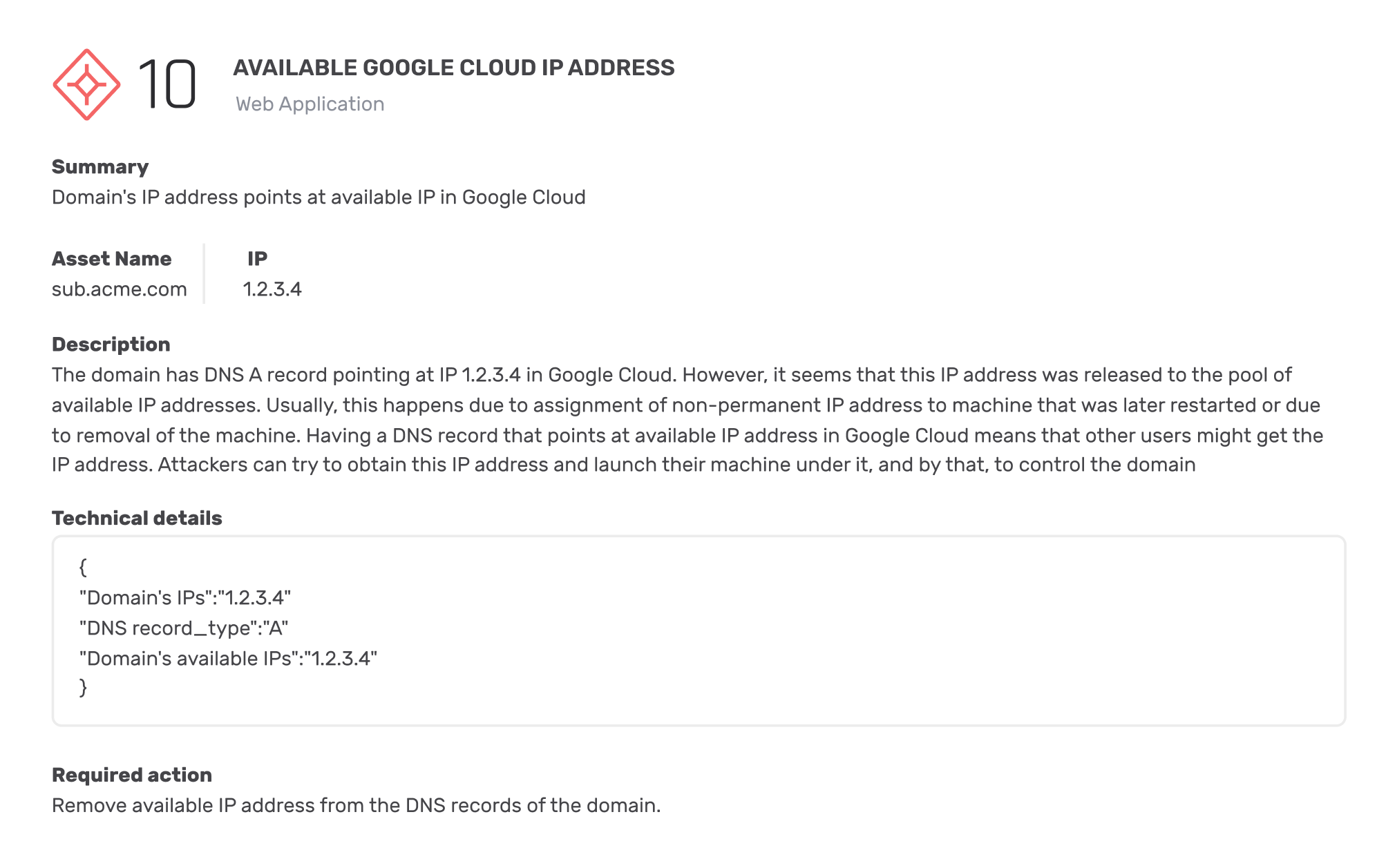
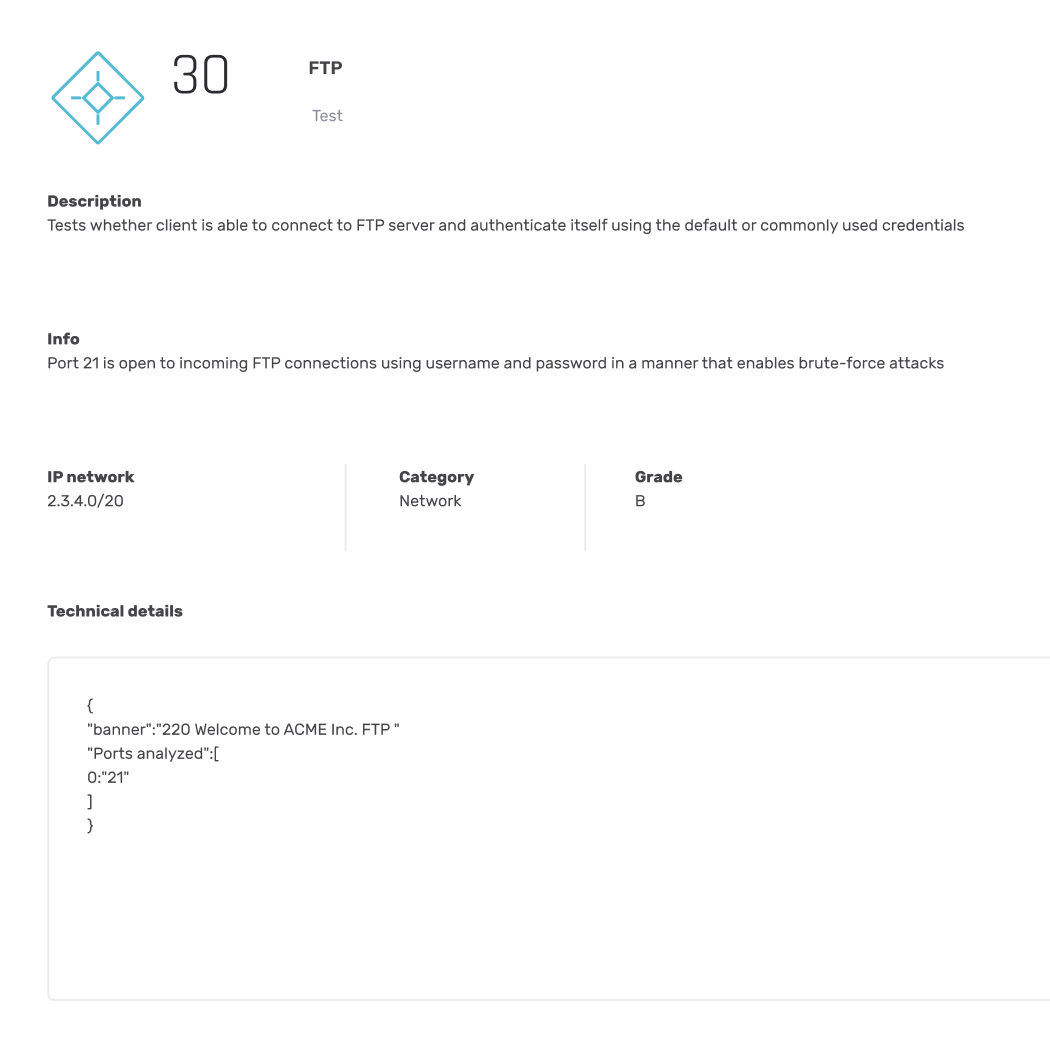
5 open FTP services that are vulnerable to bruteforce attack were detected in the organizational networks
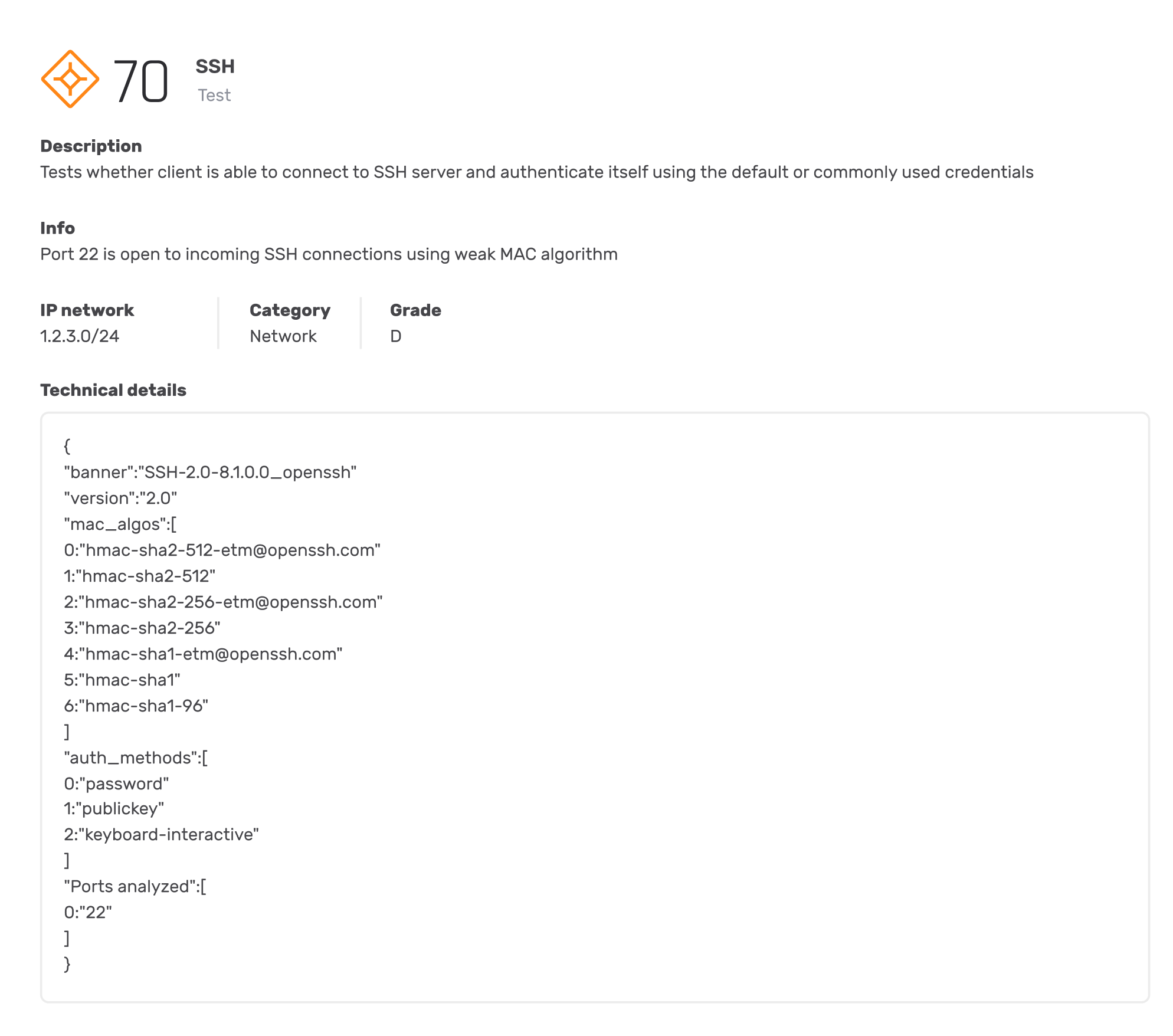
6 open SSH services that are vulnerable to bruteforce attack were detected in the organizational networks
[POPUP: #form]